Implementing the Etherhiding technique
2025. 11. 10.
OSINT 협회
OSINT 정보
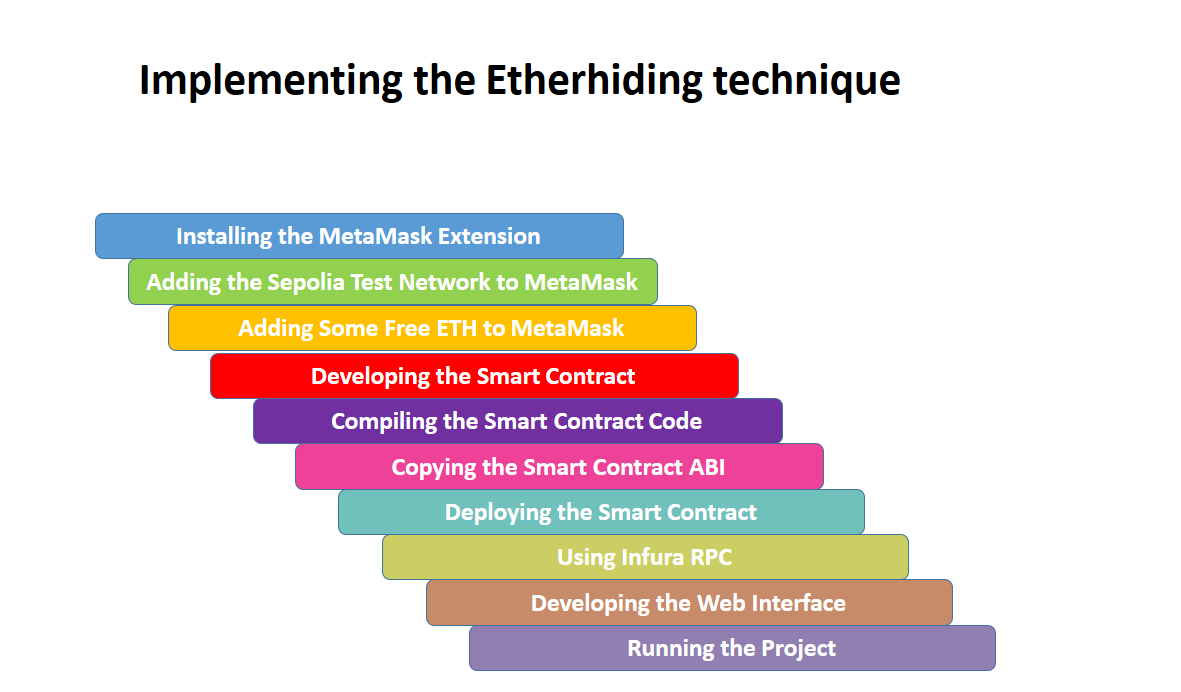
Implementing the Etherhiding technique
Google recently published reports about a new technique called “Etherhiding.” The reports explain how the threat actors UNC5142 and UNC5342 use Etherhiding — leveraging public blockchain capabilities — to distribute malware.
게시일: 2025. 11. 10.
출처: OSINT 협회 Facebook